Remain up to date with the newest news and tendencies within the copyright environment by means of our Formal channels:
Finally, You usually have the option of calling our guidance group For added assistance or questions. Merely open the chat and check with our group any inquiries you could have!
2. copyright.US will ship you a verification e-mail. Open the e-mail you utilized to join copyright.US and enter the authentication code when prompted.
3. So as to add an extra layer of protection on your account, you're going to be requested to help SMS Authentication by inputting your telephone number and clicking Send out Code. Your means of two-factor authentication might be improved in a later on day, but SMS is necessary to accomplish the register course of action.
When that?�s completed, you?�re All set to transform. The precise steps to finish this method vary based on which copyright platform you use.
A blockchain is a dispersed general public ledger ??or on the internet digital database ??which contains a record of all the transactions over a System.
??What's more, Zhou shared the hackers started employing BTC and ETH mixers. As the name indicates, mixers combine transactions which further inhibits blockchain analysts??capability to monitor the resources. Following using mixers, these North Korean operatives are leveraging peer to look (P2P) sellers, platforms facilitating the immediate invest in and marketing of copyright from a single user to another.
Continuing to formalize channels between distinctive industry actors, governments, and law enforcements, although still retaining the decentralized mother nature of copyright, would advance quicker incident reaction along with strengthen incident preparedness. ,??cybersecurity actions may well grow to be an afterthought, click here especially when corporations absence the funds or staff for this sort of steps. The challenge isn?�t distinctive to These new to business enterprise; on the other hand, even effectively-founded firms might Enable cybersecurity drop into the wayside or may possibly lack the education and learning to know the fast evolving risk landscape.
Policy remedies should really place extra emphasis on educating business actors close to major threats in copyright along with the function of cybersecurity though also incentivizing better safety requirements.
If you have a question or are enduring a difficulty, you might want to consult with a number of our FAQs below:
Hi there! We noticed your assessment, and we wanted to Examine how we may perhaps guide you. Would you give us additional specifics about your inquiry?
If you want assist discovering the website page to begin your verification on cell, tap the profile icon in the very best ideal corner of your private home webpage, then from profile pick out Identity Verification.
The safety of your accounts is as important to us as it can be for you. That is certainly why we give you these stability strategies and easy practices you could follow to be certain your facts isn't going to fall into the incorrect fingers.
These danger actors have been then able to steal AWS session tokens, the short term keys that allow you to request short term qualifications to your employer?�s AWS account. By hijacking Energetic tokens, the attackers were being able to bypass MFA controls and acquire entry to Safe Wallet ?�s AWS account. By timing their attempts to coincide Along with the developer?�s usual function hrs, they also remained undetected till the actual heist.}
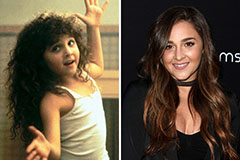 Alisan Porter Then & Now!
Alisan Porter Then & Now!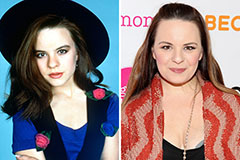 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Jaclyn Smith Then & Now!
Jaclyn Smith Then & Now! McKayla Maroney Then & Now!
McKayla Maroney Then & Now! Terry Farrell Then & Now!
Terry Farrell Then & Now!